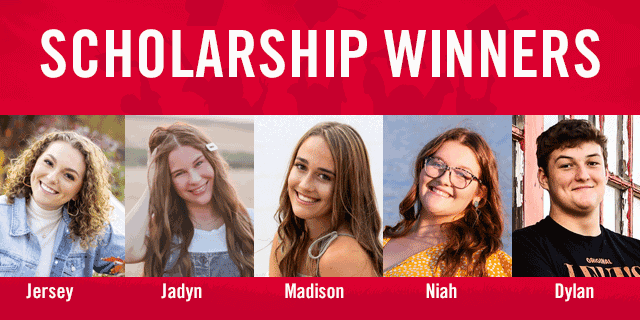
MINOT, N.D. – SRT is pleased to announce the 2022 winners of five college scholarships. Of more than 100 applications submitted by outstanding area students, four winners were awarded the SRT Scholarship for $1,500 each. The SRT $2,500 Technical Scholarship winner was also selected.
The $1,500 SRT Scholarship recipients are:
- Jersey Johnson – Minot High School
- Madison Moberg – MLS Mohall High School
- Jadyn Sandy – Velva High School
- Niah Wollenzien – TGU Towner High School
The winner of the $2,500 SRT Technical Scholarship is Dylan McDonald of Glenburn Public School, who will be attending the South Dakota School of Mines and Technology and will major in engineering or computer science.
“SRT awards scholarships to recognize our area students’ exceptional achievements and support their promising college goals,” said Cassidy Hjelmstad, SRT CEO/General Manager. “As always, we received many impressive applications. It’s been an honor to see how much this scholarship program impacts area youth and we are happy to play a small role in their success.”
Applicants for the SRT Scholarship Program were judged on their scholastic performance and achievements, as well as volunteerism and community involvement. Students were required to write an essay discussing how technology has impacted their experience as a student, whether positively or negatively, during the COVID-19 pandemic.
The SRT Technical Scholarship also required students to submit their volunteerism and community involvement, scholastic performance, and an essay describing how they can use their education and technology to reach rural and underserved populations. Additionally, a letter of recommendation from a community member or educator was required. This scholarship is unique in that it can be awarded to a graduating high school senior or an undergraduate student currently enrolled in a two-year or four-year college.
SRT congratulates the winners and wishes all seniors the best in their future endeavors.
SRT Communications, headquartered in Minot, North Dakota, is the state’s largest telecommunications cooperative. Established in 1951, SRT employs nearly 200 people and serves more than 48,000 customers across north central North Dakota. SRT is committed to bringing the benefits of fiber to rural and urban communities alike and earned the distinction as a Certified Gig-Capable Provider in 2017. Services include internet, TV, phone, and security/surveillance systems for home and business.
###